Just opening discussion, haha!
I mean if non-proton conversation isn’t allowed, I’m just comparing, haha lol!
Okay seriously though.
The three services I’m exploring are:
- Email (with email aliases)
- VPN
- Cloud Storage
I think that, if we want something fash-resistant we probably need something by a worker co-op where the whole org has to be fash to be a problem. I’m not aware of such services. A non-profit like Proton is next on the list. I’m not aware of another non-profit email provider. Tuta seems interesting but they’re for-profit.
Also any of those should be based somewhere in Europe since the US regulatory regime is weak and about to get weaker. Email isn’t end-to-end encrypted so its privacy depends on the regulatory regime of the provider.
It’s times like this that make me thankful Lemmy is written by a bunch of tankies, even if they’ve banned me.
Honesly, Lemmy Dev’s political opinion is irrelevent, thet don’t control anything outside of lemmygrad and lemmy.ml
They tried to though. Dessalines was trying to hard code a very egregious set of censored “hate” words into the Lemmy back end for a while before the (still tiny) community threw a huge shit fit about it.

If Dessalines doesn’t like hate speech, why is his second in command doing it?
Yea, that isn’t gonna fly in modern day Lemmy. I’m sure there are non-tankie programmers that are willing to work on a fork, that’d definitely splinter Lemmy into 2 different “fediverses”, one under the tankie branch, one under the new non-tankie fork. I don’t think the devs want that. They seem to be very anti-corporate, and such a move that would splinter the Lemmy community would only benefit big tech.
Oh yeah. It took me a while to figure out they have much more in common with my interest than the wealthy techbros.
Nubo is run by/as a co-op if that’s your vibe?
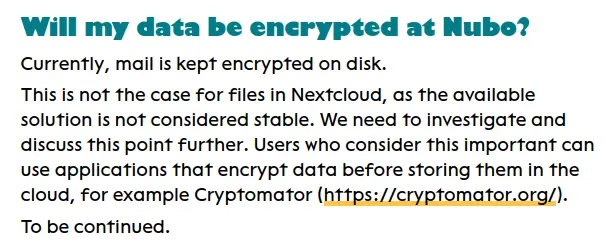
Hm. Is this production Nextcloud and email run by a coop? This might indeed be what I’m looking for. I don’t need someone’s proprietary software. Well run FOSS in the cloud might be more than enough.
The only down site is that it don’t look like the data is end-to-end encrypted.
I need to start paying attention more, how was this under my radar?
Having said that, your link isn’t working for me. For anyone else: https://www.nubo.coop/
That’s pretty cool, though their prices for cloud storage are a little higher than I was hoping for.
Honestly, it is my expectancy that if the US goes down that worst possible outcome, and they start passing laws that make you worry about your communications, then the “US Cyber Defense Platform(Great Firewall)” will also be quick to pass, argued to protect the children from porn, rights holders from piracy, and of course will quickly expand to any service that doesn’t agree to an encryption back door so they can look for “terrorists”.
In that case, Proton and any non-surveillance allied service is out. Email as we know it is pretty unsafe, and if you want to use email privately you will have to learn to provide your own encryption via PGP and the like, most likely through your own server even, and you will stress to ensure proper configuration.
Or get to another method(like Matrix configured for E2E) before they get pulled from your App Store for not complying with the Patriot Act 2.0, and be ready to learn the safest way to sideload updates, and how to dodge around the Bigly Firewall to connect with international users.
Honestly, if it went that far, They could just outlaw encryption altogether. Require all SSL to include their back door and they DPI everything on the way through. If anything doesn’t work on the DPI, they log it and drop it. We’ll end up having AI write us novels where you can take predetermined word order to create encoded messages
If it went that far, we’d be back to offline communication and small communities, because the AI would be programmed to tattle on us. :)
It’s a fascinating question actually how far technology could be used against us, and how long the “underground” could continue to use it before we’d have to continuously invent something completely new just to communicate, until we just loop back around to word of mouth or smuggled paper missives. A lot of people think that the cat is out of the bag on mass communication, that we can never be silenced again but I’m never quite so sure…
I don’t know, I’m kind of excited about moving back to code talking and pulling select passages out of books.
Email:
- mailbox.org
- tuta
- hushmail
VPN:
- astrill (expensive but awesome)
- mullvad
Cloud storage:
Rent a small server / vps and set up your own nextcloud instance. Even some packages meant for webhosting work, as long as you can install custom php applications. I’m using all-inkl.com (private plus package) and got 500GB allocated to my nextcloud instance.
astrill (expensive but awesome)
Rule No. 1 when it comes to VPNs: NEVER trust a VPN service that claims to be anonymous. VPNs aren’t anonymous. Only Tor is anonymous.
Likewise, never trust that tor is completely anonymous. There are a limited number of tor nodes, and an extremely limited number of exit nodes. The barrier to entry to stand up thousands of nodes is simply a cash problem. It certainly beyond the reach of most corporations, But I wouldn’t want to do anything on tor that would draw the ire of a large government agency.
They all claim to be anonymous. And yeah, nobody can independently validate the no logs policy, even Mullvad that has been security audited doesn’t let anyone near their production environment, so what they release to the testers might not be identical to what they use live.
Calling TOR anonymous is a big stretch through, a bunch of commits to the code have been traced back to the CIA if I remember correctly, and various intelligence agencies worldwide are running exit nodes and log everything they can get their hands on. Whether they can decrypt it with current tech is another story, but you better believe they don’t just delete it.
Interesting, they even host their own Mastodon instance.
What makes astrill special? Since they are really expensive.
Their absolute BS marketing. They claim to make you anonymous, which is impossible for a VPN provider. Never trust a service that claims such bullshit.
They run a proprietary protocol that works in China and Saudi Arabia, where other protocols are known not to work. I’ve lived in China for 7 years, and Astrill never once let me down, while Express, Nord, Proton and a bunch of others hardly ever worked.
@Tutanota@mastodon.social hasn’t responded yet to whether it’s possible to migrate emails from proton to tutanota. Proton Mail has an export tool, but I couldn’t find an equivalent import nor export tool for tutanota :/
I have been mulling over Posteo for encrypted mail. Looks like a lot of the same benefits as mailbox.org, but my main attraction was the price (one euro per month) and fact that they do not associate payment with your email account. Haven’t done a deep dive but will compare to mailbox.org before I pull the trigger.
Their canteen is also vegetarian 👆
Does that make the emails more secure?
Posteo is great, no issues in 2 years (not forever, I know, but it’s what I got)
I wish their UI were better though…
Thanks for the recommendation. What domain do you use for your email address, if you don’t mind my asking? Sounds like there are country codes available, but I’m not sure how relevant they would be to the address.
Personally, for a vpn, I really like airvpn. It has been around for ages. It’s not huge. It’s (seems to be) run by some very nice and super tech-savy people.
No, it’s not the fastest. Their default VPN client (eddie, which is just openvpn heavily customized, and is open source) can be clunky, but they support wireguard and regular openvpn connections with a generated config.
A lot of people use it for, uh, sharing Linux iso’s, but as a regular VPN service they are pretty awesome as well. They even have a way to tunnel their VPN connection over tor (https://airvpn.org/tor/) which is quite handy depending on where you are. And the Android client can spoof your GPS info to the country where their server is located.
As far as cloud storage goes, run my own nas, and have wireguard tunnel to my house which allows me to access it for any of my cloud storage needs.
NeutronI assume here you want to explore the three services individually, because putting all the eggs in the same basket is dangerous. In which case, Mozilla has a VPN service that builds up on someone else’s (Mullvad I believe?). Dunno what to suggest on the other two fronts.
Not tried it myself: https://disroot.org/en
They are fine. They seem disorganized, I wouldn’t use them as a primary personally, but I’ve used them as a side account for years.
I would prefer a service with MFA
Zoho mail + office suite + cloud storage/sync is only $3/month and good encryption and Mullvad VPN has locations all around the world, fast speeds, and a proven dedication to privacy for €5 a month.
For email, Startmail seems interesting. It was rated pretty high on PCMag.
https://www.startmail.com/pricing
Curious if people’s thoughts.
What legal jurisdiction do they operate in? I see German and English versions of their site but nothing in About Us on jurisdiction.
The Netherlands.
The about section has this:
European privacy
We believe that privacy is a fundamental right, and that email communications should be private and secure. StartMail is independent from any commercial third parties or governments. Our headquarters and servers are located in the Netherlands, ensuring that your emails and data are protected by the European Union’s General Data Protection Regulation (GDPR), the world’s highest privacy standard.
This looks great although i cant seem to find any mention of Open Source work they do? Thats something i really like about Proton.
Email address with StartMail domain or one custom domain
Proton has a similar restriction which is a bummer.
FWIW Startmail doesn’t have any calendar feature, which is ridiculous in this day and age.
In regards to email aliasing services, addy.io is the only one I know of other than SimpleLogin, which is owned by Proton AG–so if you want to get away from Proton, SimpleLogin isn’t an option. Both of these services are recommended on privacyguides.org.
Some email services allow you to use a domain you own, which theoretically should give you unlimited aliases to work with, but may not be as privacy-focused as the email address is only as anonymous as your registered domain.
Personally, I prefer the ‘pseudonymous’ aliases that addy.io and Proton Pass give (it’s usually something like
random.words123@passmail.netin the case of Proton).If anyone has good experiences with other aliasing services that provide this option, please let us know.
How about just a mail service with a catch-all option? If you send an email to my domain that doesn’t match any of my known addresses, it ends up in a catch-all box. That box order deletes mail every month and I just check it when I need it.
I have had good experiences with https://www.ovpn.com/ as a VPN provider.
I love downvotes for providing a throrougly explained response to a question of opinions
*VPN
As much as some people discount its use/viability, tor (as in tor anonymizing network layer service, not Tor browser) is an excellent alternative to a VPN. IMHO.
It is free. It is open sourced. It is highly configurable. You can select your exit nodes (country) should you choose. You can use it to route all or any traffic. It also handles anonymous DNS resolving if you like.
You can run it as a service or instance on Linux on its own and you can use dnscrypt-proxy or other secure DNS with it. As a proxy or VPN on android via a number of apps and in combination with others. (Invizible pro can use dnscrypt over tor and run as proxy or vpn. RethinkDNS can do basically the same. Orbot is its own tor proxy. Etc)
Every node may not be able to handle your traffic needs, but it shouldn’t be hard to find one that can. VPN apps face similar issues.
*IVPN is a Canadian vpn provider that hosts several tor nodes and funds the tor organization. They have a reputation for serious privacy and security.
*Email :I’m here to learn what others think.
*cloud storage: I’d say the best option is your own option. Nobody to worry about in the middle. I use ssh and simple servers set up on my machines.
The self hosting community could provide a lot of info on how to set up.
https://lemmy.world/c/selfhostedHistorically, people have gotten caught with their hands in the cookie jar while using tor. Most of the documented cases have been from DNS leaks and the like through targeted attacks.
Theoretically it’s possible to own enough of the intermediate and exit nodes to collect meaningful data about who’s using it and where they’re going. It’s just very difficult and expensive.
I only give it maybe 50/50 odds let the feds have this power, but that’s not particularly rosey for a security product.
From the backbone perspective,VPN traffic absolutely gets monitored on the way out, and they can probably tell everyone that is on the VPN provider at the moment. But timing attacks are rough through a busy crypto tunnel. Your protection basically rolls down to whether they’re keeping logs, whether somebody’s monitoring the backbone around them, and if there’s any point in time where the traffic on the VPN is low enough that they can correlate traffic in with calls out.
Unless you’re pissing off the feds I doubt tor is any better off than VPN.
I don’t think I’m important enough to piss off feds. I have opinions, but I am not active in the ways I was 30 years ago.
I am no expert, but I am an avid and voracious learner and geek.
I do use a variety of vpns and proxies. I switch often. I also relay certain things to certain things permanently.
I am especially aware of DNS . one of the first major learnings of my Linux use was setting up a secure DNS proxy. It was a pretty intense learning curve. 6 or so years later, I’m fairly comfortable with most aspects of it and securing connections and avoiding data leaks.
I use anonymizing dnscrypt-proxy with local doh. I use other secure DNS protocols and servers when/where required, or desired.
I check for leaks often. I have a few scripts that I wrote to make sure things don’t. I use a few sites to do checks. I use nmap to scan all my things.
I use tor for some things. I use proton for others. Warp for others. Shadowsocks for others. Calyx and other services for other things.
I always use a trusted bridge or proxy to connect.
I run a snowflake proxy sometimes.
I don’t do illegal stuff.
That said, what is legal now may not be if/when some dictator decides. With that in mind, I appreciate my privacy and intend to keep it any way I can.
I’m beyond exhausted, so I hope I made sense.
Given the, for most people, complete uselessness of VPN I think Tor is an excellent thing to highlight. But if I were to use a VPN, it would be mull.
Email: posteo is great, $1/mo, good balance of security without going crazy given that mail is insecure. Plus the people who operate it seem like good people.
Storage: agreed, I use syncthing for my critical files (encrypted of course). However not having at least a little bit of off-site backup seems insane. For me thats music, password files, and images of critical docs like passport, birth cert, SS/selective service card, etc.
Don’t forget password manager. Oh, and we’ll need a service that combines all of those into one monthly subscription, and for as low a price as Proton.
Has anybody used KolabNow for email? It’s the hosted version of Kolab which is opensource
They have an OK price, I think of 5 CHF/month (swiss francs).
They also have email import, which combined with Proton Mail’s export tool, allows a manual, but traditional migration. (More features). I also like that they support SMTP and IMAP, but I don’t know how that works with E2E encryption 🤔
Looks interresting…