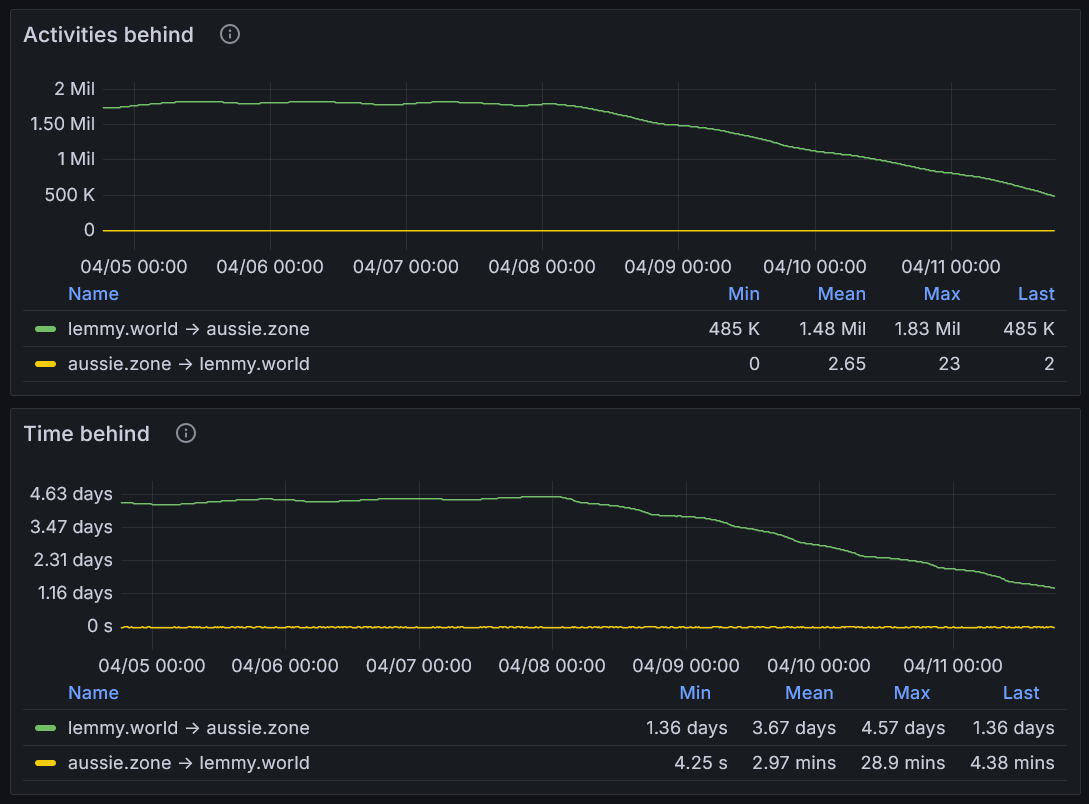
Still on track to be caught up late tomorrow :)
I also have backup accounts on these instances:
https://beehaw.org/u/lodion
https://sh.itjust.works/u/lodion
https://lemmy.world/u/lodion
https://lemm.ee/u/lodion
https://reddthat.com/u/lodion
Still on track to be caught up late tomorrow :)

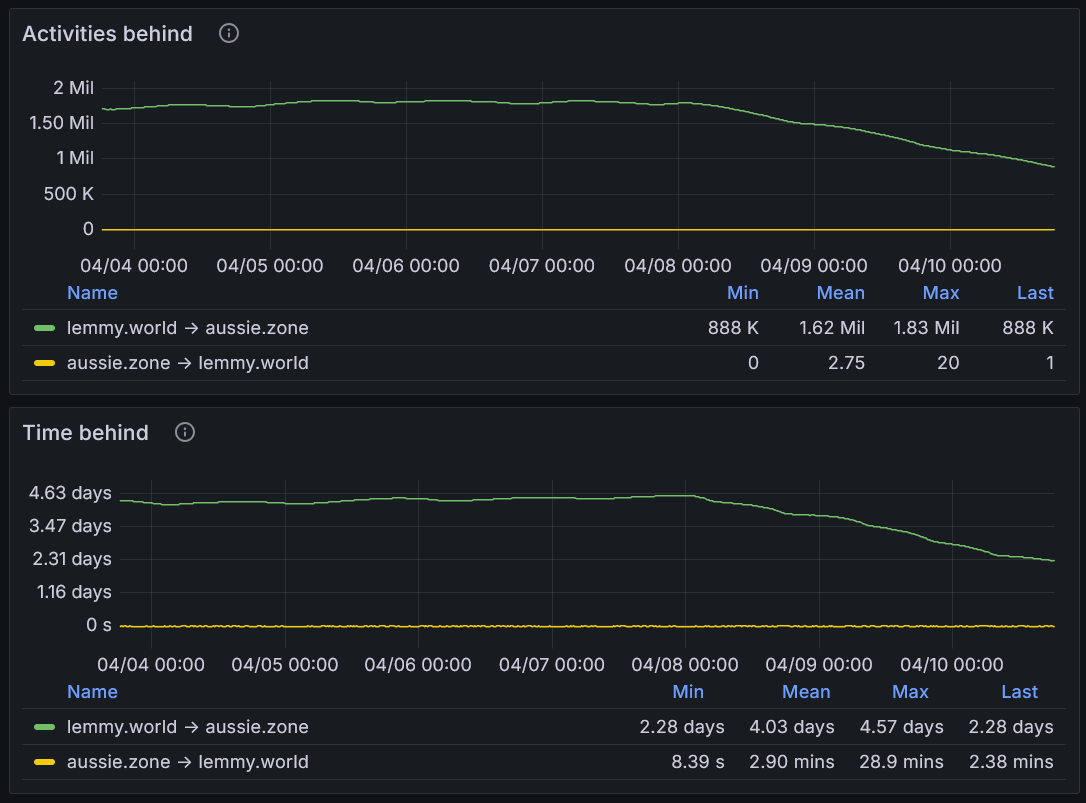
At the rate we’re catching up, I think we’ll be all caught up Saturday some time:
It’s a simple tick box in the admin settings interface. Trivially easy to enable, and presumably disable. Doesn’t appear to even require a service restart.
It’s not so much about cost, but impact on user experience when the server is busy serving non-logged in users.
It’s not usually a concern, but having this in place would have mitigated the recent “attacks” we experienced without me having to do anything.
I’m not talking about making this community private. Its valuable as is.
0.19.11 adds the ability for an instance to not display content to non-logged in users. Non-AZ users would retain access to all AZ homed communities etc.
As posted elsewhere, LW admins have enabled concurrent outgoing federation ~12 hours ago which has greatly improved things:
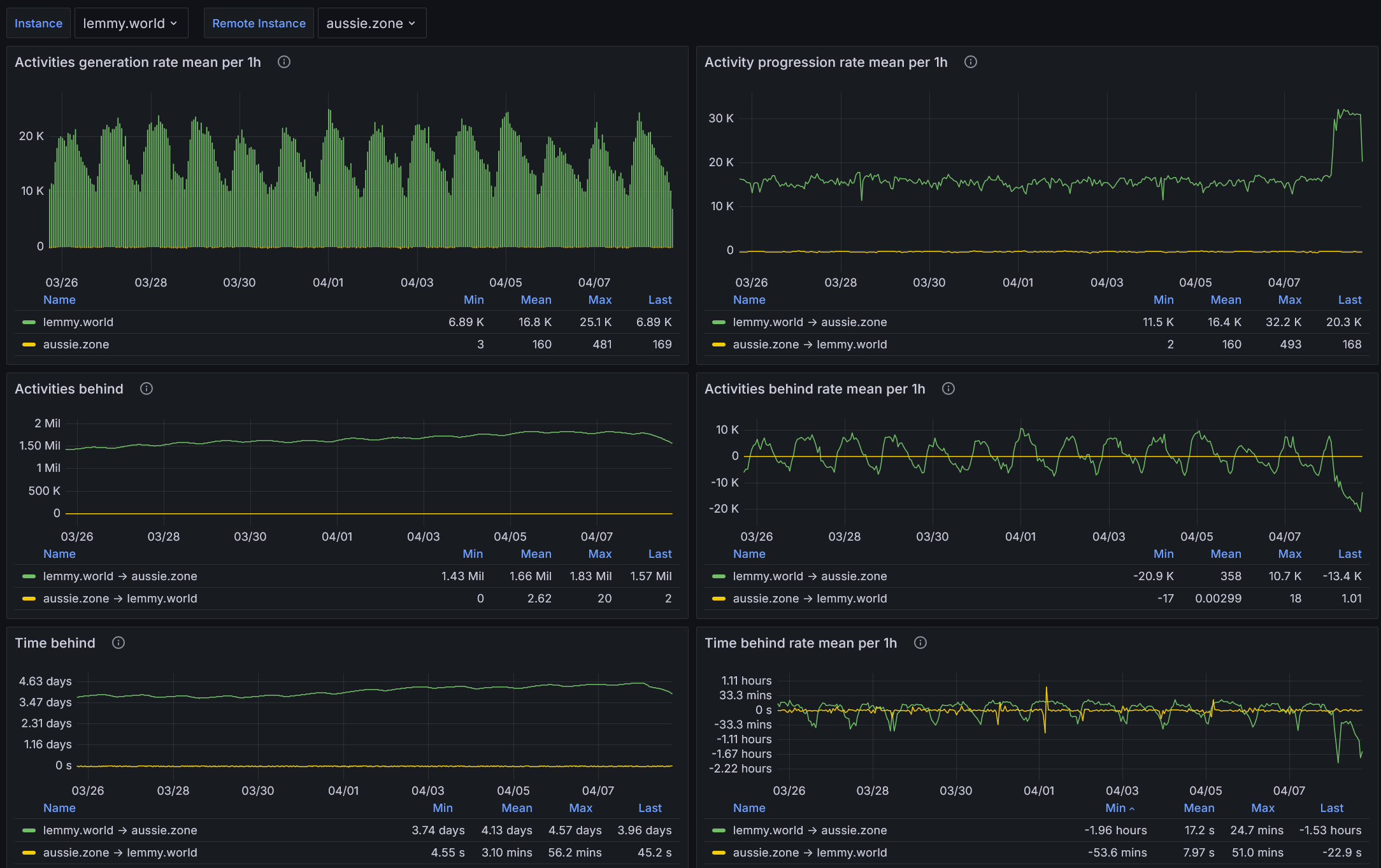


They’ve turned this on overnight after it came up in an admin chat channel, we’re no longer falling behind but are catching up at a good rate. Once caught up, federated activity from LW -> AZ should be pretty snappy and remain that way.
Yep, /c/meta is the perfect place to discuss this. Or anything else meta relating to AZ.
Have reached out to LW admins, they’ve enabled 2 send threads… looking better now… will keep an eye on it.


Thanks, I hadn’t seen this one. I’ve updated our nginx config and AZ now passes the test on that page. No idea if it will help with GIFs etc.
And for anyone curious… blue line is traffic from a country we don’t normally see much traffic from. The unusual spike, then drop when I blocked the specific sources:
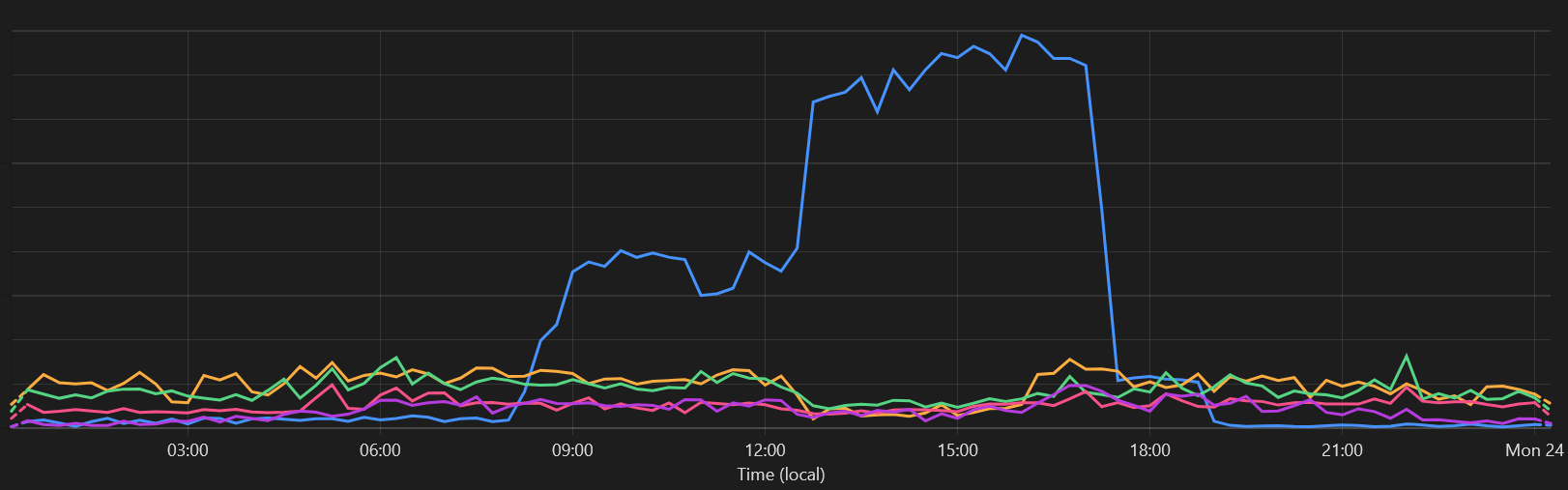
The traffic stopped a few hours back, from all IPs at once. Definitely seems to have been some sort of deliberate action.
The unusual traffic all appeared to be coming from one location on the internet, with the same user agent string. Any traffic from that network will now receive a captcha from Cloudflare. I’m not aware of any lemmy instances hosted there, but will keep an eye on things.
For some context, CPU usage jumped when the traffic started… and dropped after the block was applied:
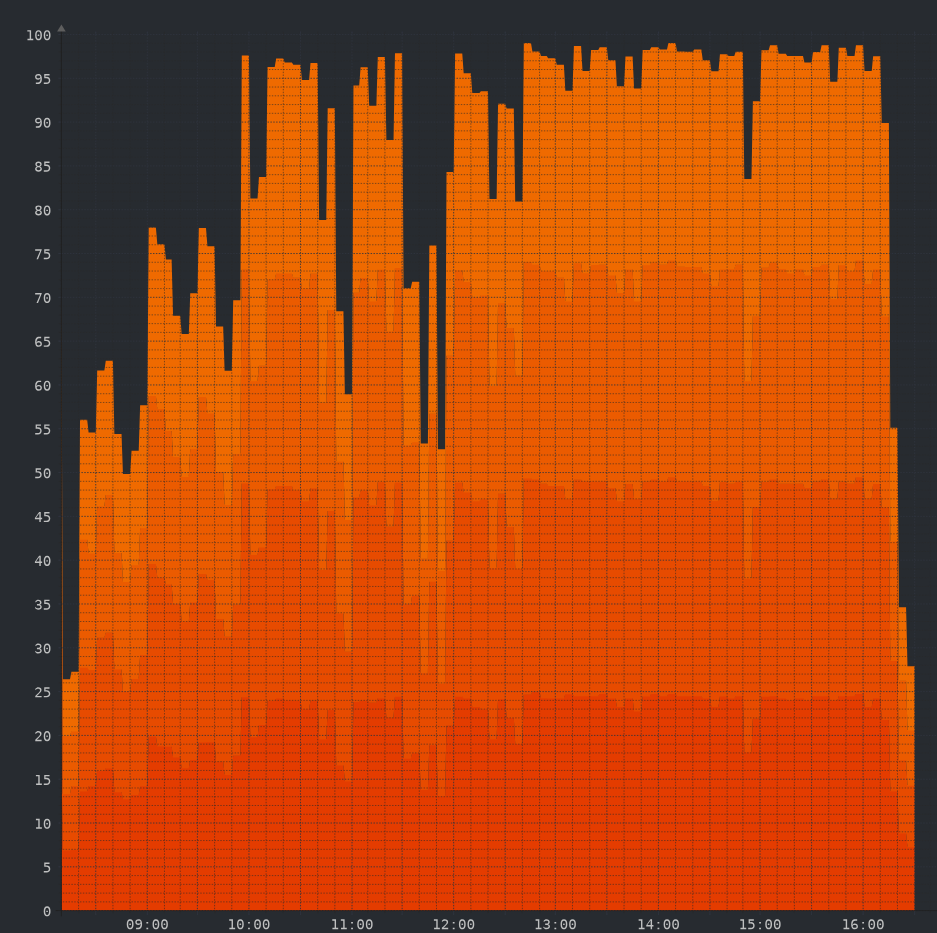


It sure doesn’t feel like autumn so far


Not sure how I should feel that the bubble I live in seems far more accepting and empathy towards asylum seekers.
I don’t think the people I live/work/socialise with are particularly extreme… but according to this we’re collectively not representative of wider Australian views.
I choose to believe their sampling was flawed and somehow only sampled the worst of us.


If you’re posting as an uninvolved third party about an event you’re interested in, it’s not an ad.
As for spam, if you post a ridiculous volume about such events it could be construed as spamming. So long as you’re manually posting this shouldn’t an issue.
Basically, don’t be trying to sell anything or abusing the AZ site.
Don’t get me wrong, I’m happy you posted this. If there are unvoiced concerns or issues, here is a good place to discuss them.
I’m not as active on lemmy as I’d like, so I’m likely not aware of issues unless they’re raised somewhere like this.
For potential meta issues such as age verification, I’ll be seeking input from the community when they arise and information around them is known and understood.



























Probably both this and cloudflare caching. Looks like I set CF to cache for 1 year at some point, I can lower it… but that won’t “fix” this, only limit the time its an issue for.